Proactive Endpoint Protection with AI-Driven Threat Detection & Response
Detect, contain, and remediate endpoint threats in near real-time
Overview of the Product
IBM QRadar EDR helps organizations protect their most vulnerable assets—endpoints—by delivering real-time detection and autonomous response to advanced threats. Built for today’s evolving attack landscape, QRadar EDR combines continuous learning AI, attack visualization, and NanoOS-based visibility to help security teams identify and contain both known and unknown threats quickly. With native integration into IBM Cloud Security and Compliance Center, it enables unified threat detection and compliance readiness across hybrid environments.
Why Choose QRadar EDR?
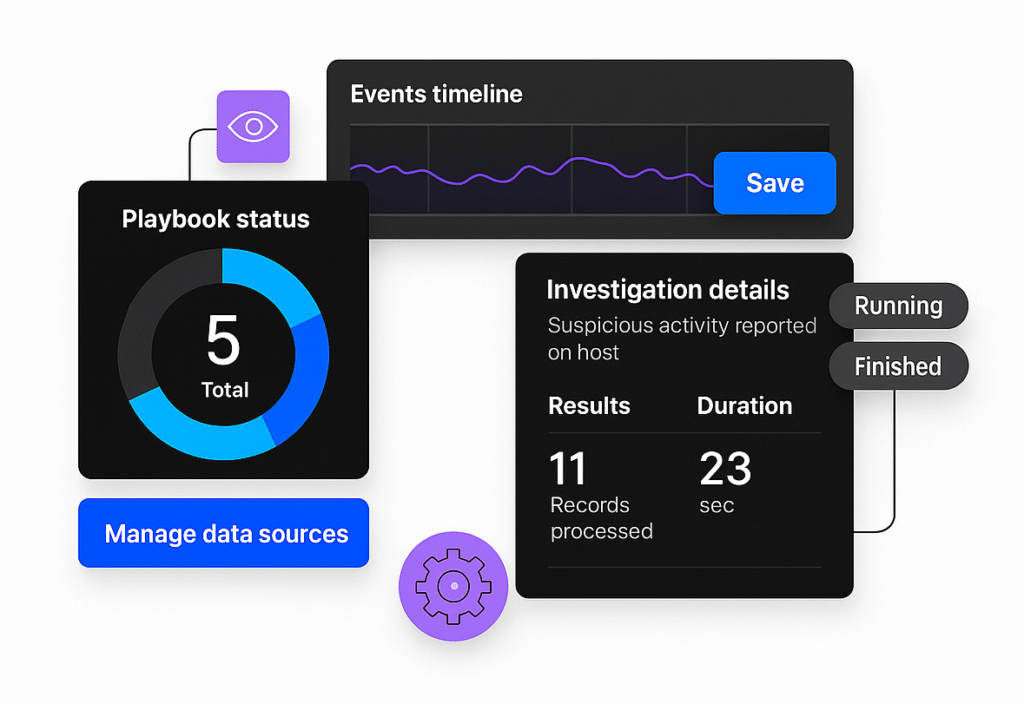
Gain deep insights into all running processes and applications with undetectable NanoOS technology.
Continuously learning AI automates detection, alert triage, and guided remediation with minimal analyst input.
AI-powered alert management reduces false positives by up to 90%, allowing teams to focus on real threats.
Visualize attacks with behavioral trees that accelerate investigation and simplify response workflows.
Tailor detection use cases via scripting to meet organizational or regulatory needs—no reboot required.
Choose SaaS or on-premise deployment to meet data sovereignty, regulatory, or air-gapped environment needs.
What the Numbers say?
Features
An AI-driven alert manager that learns analyst behavior to deliver faster, more accurate recommendations.
Visualize threat progression from initial breach to resolution, with guided investigation and containment.

Detect and stop advanced ransomware campaigns with near real-time behavioral analysis and response.

Create advanced custom rules to detect anomalies without disrupting endpoint performance.
Manage all severity levels with automated investigation and threat handling.

Isolate endpoints, kill processes, and apply blocking policies from a single unified interface.
Key Facts
Choose the deployment method that suits your compliance needs.
Handles alert fatigue, enabling junior analysts to act with expert-level precision.
Ensures cohesive policy enforcement and compliance tracking.
Case Studies
Protecting Critical Airport Operations with IBM Security QRadar EDR
A major international airport leveraged IBM Security QRadar® EDR (Endpoint Detection and Response) to detect, analyze, and remediate malware threats across its hybrid IT infrastructure without disrupting operations. With over 1,000 daily flights and 70 million annual passengers, the airport required a robust cybersecurity solution capable of identifying sophisticated attacks in real time while maintaining continuous operational uptime.
Business challenge
As one of the world’s busiest airports, the organization faced constant cyber threats targeting its critical IT and operational systems. With thousands of connected devices and networks managing logistics, passenger processing, and flight operations, even a minor disruption could lead to major service interruptions.
The airport needed to:
- Strengthen its endpoint detection and response (EDR) capabilities.
- Prevent, isolate, and remediate advanced malware attacks in real time.
- Gain complete visibility across distributed systems and endpoints.
- Protect airport operations without impacting performance or uptime.
Solution
To enhance its cybersecurity posture, the airport deployed IBM Security QRadar EDR, a next-generation endpoint protection platform powered by AI-driven threat detection and automation. The solution continuously monitored endpoints across operational and IT environments to detect malicious behavior patterns before they could cause disruption.
Using QRadar EDR’s real-time visibility, the airport’s security team was able to detect suspicious network activity linked to malware infiltration, analyze the threat, and initiate automated remediation — all without interrupting airport operations.
Solution components
- IBM Security QRadar EDR
- IBM Security QRadar Suite Integration
- Advanced Threat Detection and Response Framework
Real-Time Detection & Remediation
QRadar EDR provided AI-powered behavioral analytics to detect anomalies at the endpoint level and automatically initiate containment measures to prevent lateral movement.
Non-Disruptive Security Operations
The platform ensured remediation processes were executed seamlessly, allowing the airport to maintain uninterrupted passenger and flight services during active threat resolution.
Comprehensive Threat Visibility
Through centralized dashboards, the IT team gained full visibility across thousands of endpoints, enabling proactive detection, investigation, and recovery from potential attacks.
Result
- Identified and neutralized advanced malware before system compromise.
- Reduced detection and remediation time from hours to minutes.
- Achieved full endpoint visibility across IT and OT networks.
- Prevented service disruptions and ensured uninterrupted flight operations.
- Strengthened cybersecurity resilience through automation and AI.
IBM Security QRadar EDR gave us the power to detect and eliminate threats in real time — even across complex airport systems — without affecting daily operations. Its automation capabilities have made our response faster, more precise, and more reliable.
— Head of Cybersecurity Operations, Major International Airport
Safeguarding Critical Infrastructure with IBM Security QRadar EDR
A major European water management facility responsible for supplying clean water to over 3 million residents enhanced its cybersecurity resilience using IBM Security QRadar® EDR (Endpoint Detection and Response). By integrating advanced endpoint protection and AI-driven threat detection, the facility minimized downtime, prevented potential contamination risks, and ensured uninterrupted delivery of essential water services.
Business challenge
The water management facility’s operational technology (OT) systems play a vital role in regulating water purification, pumping, and distribution. However, its reliance on legacy infrastructure made it increasingly vulnerable to malware and ransomware attacks.
The organization needed to:
- Detects and contains cyber threats across IT and OT systems.
- Prevent disruption to automated control systems managing water flow.
- Enable real-time visibility and faster remediation of security incidents.
- Strengthen protection for critical infrastructure in compliance with EU security mandates.
Solution
To fortify its cyber defense, the facility deployed IBM Security QRadar EDR, a robust endpoint detection and remediation platform designed for industrial environments. The solution’s behavioral AI models identified suspicious endpoint activity and initiated automatic remediation within seconds — stopping threats before they could impact operations.
Working closely with IBM Security experts, the facility implemented QRadar EDR across its control networks, achieving seamless integration with existing SCADA and OT systems. The deployment provided full visibility into endpoint behavior, enabling early detection of anomalous activities and automated containment of infected devices.
Solution components
- IBM Security QRadar EDR
- IBM Security QRadar Suite
- AI-Based Threat Detection and Remediation
Rapid Threat Detection
AI-driven behavioral analytics enabled detection of malicious activity within seconds, providing early warning before any system compromise occurred.
Automated Containment and Remediation
QRadar EDR isolated infected endpoints and executed automated cleanup actions without disrupting operational processes or water flow systems.
Industrial Environment Integration
The system was tailored to protect industrial control systems (ICS) and OT environments, ensuring cybersecurity compliance and operational continuity.
Result
- Detected and remediated malware threats within 2 days of deployment.
- Prevented service disruption and ensured 100% operational uptime.
- Reduced mean time to detect (MTTD) to seconds.
- Strengthened infrastructure protection and EU compliance posture.
- Enhanced confidence in critical water supply operations.
IBM Security QRadar EDR gave us the visibility and automation we needed to protect critical operations. The ability to detect, isolate, and remediate threats in real time prevented downtime and safeguarded essential public services.
— Chief Information Security Officer, European Water Management Facility
What The Users Say

“Security analysts report faster triage and improved visibility using QRadar EDR�s visual storyboards. With seamless integration into IBM Security� QRadar� SIEM and the IBM Cloud Security and Compliance Center, customers appreciate how QRadar EDR enhances both threat detection and compliance readiness.”
FAQ's
What is IBM QRadar EDR used for?
QRadar EDR (Endpoint Detection and Response) provides advanced detection, investigation, and response to endpoint threats. It helps identify suspicious behavior and contain attacks in real-time.
How does QRadar EDR detect threats?
It uses behavioral analytics, MITRE ATT&CK mapping, and machine learning to detect anomalies. These techniques allow it to catch threats that evade traditional antivirus software.
Can QRadar EDR perform automated responses?
Yes, it can automatically isolate infected endpoints, terminate malicious processes, and rollback system changes to stop attack spread quickly.
What types of endpoints does QRadar EDR support?
It supports Windows, macOS, and Linux systems, making it adaptable for diverse IT environments with both servers and workstations.
How does it support incident investigation?
QRadar EDR provides detailed attack timelines, memory forensics, and process tracing to help security teams understand and respond to incidents quickly.
Is QRadar EDR part of a larger security suite?
Yes, it integrates with QRadar SIEM and SOAR, enabling a unified threat detection, orchestration, and response environment for security teams.
How frequently are threat intelligence updates pushed?
It receives continuous threat intel updates via IBM X-Force to stay ahead of evolving malware, ransomware, and zero-day threats.
How does Nexright help deploy QRadar EDR?
Nexright provides architecture design, rapid deployment, and configuration of detection policies to align with specific enterprise risk profiles.